User Guide
Table of Contents
Chapter 1: Introduction / Meet LAD
Chapter 2-1: Installation Tips
Chapter 2-3: Connecting to the Internet
Chapter 4: Configuring a Wireless Network
Chapter 5: Connecting and Managing Clients
Chapter 6: SIP Server / VoIP PBX
Chapter 6-4: Voicemail Boxes / VM Menus
Chapter 6-9: Call Routing & Processing Examples
Chapter 7: Access Controls / Parental Controls
Chapter 10: Network Security / LateralFirewall
Chapter 11: DNS Server and LateralDNS
Chapter 13: Ethernet Packet Capture
Chapter 14: Wireless Packet Capture, Monitoring and Reports
Chapter 15: Settings, NAT Forwarding / Port Mapping and Sys Info
Connecting and Managing Clients
Connecting Clients via Ethernet
To connect any device to LAD via an Ethernet connection, simply connect the cable from the device to any Ethernet port on LAD, other than the WAN port, which is typically referred to as port 1 (the WAN port must only be used for the Internet source). LAD will automatically detect the connection of the new device and create a profile for it by its MAC address, which you will be able to view within the user interface (see “Managing Clients” below).
For information on connecting clients via Wi-Fi, please see Configuring a Wireless Network.
Managing Clients
LAD automatically creates and maintains profiles for each client device connected to it. These profiles may be accessed by logging in to the user interface. Up to nine currently active client devices will be listed on the main menu page under “Active Computers and Devices.” A full list of client devices, whether active or not, may be found by clicking on “View All Devices.”
The list of client devices contains information about each device, including its IP address, most recent bandwidth utilization, packet rate and the date and time of its most recent activity. The “Disable” button manually disables the client device’s connection with LAD, overriding any other access control or firewall setting (see Access Controls, later). Take care not to disable the connection of the computer from which you are accessing LAD’s user interface. Clicking on “Reports & PCAP” takes you to a page from which you can access activity reports and PCAP data for that specific client device.
Clicking on the client device’s name will open up the general info and settings page for the individual device. The “Device Info and General Settings” section displays information about the device, including its name, status, recent bandwidth usage and MAC address, with an option to toggle its connection status. By default, LAD assigns the client device’s MAC address as the device’s name, however, you may choose to change the name to a reference or nickname of your choice, as the name has no bearing on connectivity or operations. If “Allow Internet Access” is checkmarked, LAD allows the device access to the Internet. If “Allow Local Access” is checkmarked, LAD allows the device to be discoverable to other devices on the local network. “Deny LAD Amin Access” restricts the device’s access to the LAD administrative console.
- The device's last activity timestamp will show the most recent time of Internet activity if Allow Internet Access is checkmarked, but Allow Local Access is not.
- The last activity timestamp will show the most recent time of the device's activity on the local network if Allow Local Access is checkmarked, but Allow Internet Access is not.
- The last activity timestamp counts management traffic (communications between the device and LAD) together with local activity.
Clicking on “DNS Log” opens up the log of DNS requests from the device, including responses. Click on “Reports and PCAP” to find device activity reports and to download packets.
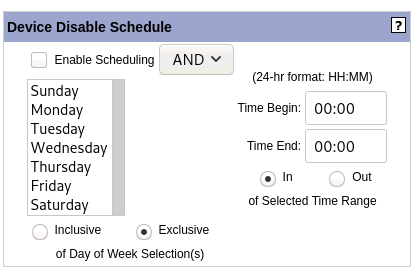
Device Disable Schedule
The Device Disable Schedule is used to enable and disable the device’s ability to connect to LAD on a Day of Week and Time of Day Schedule. Under the day of the week selections, select either “Inclusive” for the device to be disabled on the selected days or “Exclusive” for the device to be disabled on the non-selected days. Under the time of day entries, select either “In” to disable the device between the designated begin and end times or “Out” to disable the device outside of the designated begin and end times. The AND/OR selection modifies how the day of week and time range selections interact. Choosing AND makes the disable function operative when the day and time selections intersect, while OR makes the selected function operative when either of the day of week and time selections are met.
Please see Scheduling for a more detailed explanation on how the scheduling settings interact.
Device Domain Name Settings
The “Domain Name Schedule and Domains” section is part of LAD’s multi-layered DNS firewalling system. Here is set the default scheduling action for any domain name entries associated with the device, which would be listed under “DNS Exceptions” (domain name entries may be associated with a device through the Domains section of LAD’s interface. See “DNS Firewalling” for more information on how to do this). Above the list of DNS Exceptions are four radio buttons: Deny, Deny with Exceptions, Allow and Allow with Exceptions. The selection of one of these options sets the default DNS firewalling action for any domains associated with the individual device. If Deny or Allow are selected, the associated domains will be denied or allowed regardless of any separate settings on the domain page. If Deny with Exceptions or Allow with Exceptions are selected, the behavior of DNS firewalling will be affected by the settings for the domain name, i.e., the domain name settings applicable to the device will be the “exceptions.” If no selection is made, the default action is "Allow with Exceptions."
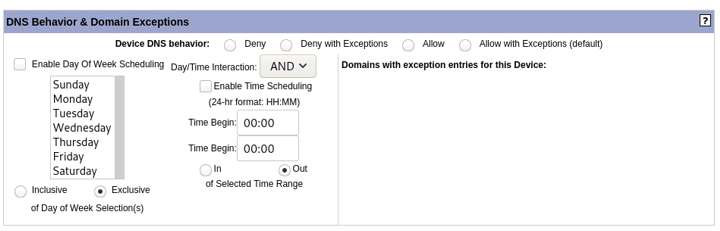
Day of Week and Time of Day scheduling is also available for the Domain Name Scheduling. Under the day of the week selections, select either “Inclusive” for the desired DNS firewalling action to take place on the selected days or “Exclusive” for it to take place on the non-selected days. Under the time begin and end entries, select either “In” for it to take place between the designated begin and end times or “Out” to for it to take place outside of the designated begin and end times. Use a 24-hour format for the time begin and end entries, e.g, 9AM would be 09:00 and 9PM would be 21:00. The AND/OR selection modifies how the day of week and time range selections interact. Choosing OR makes the day of week and time selections cumulative, while AND makes the selected function operative when the day of week and time selections intersect.
Please see Scheduling for a more detailed explanation on how the scheduling settings interact.
Some Browser Settings Hinder LAD's DNS Controls
Some browser settings will interfere with LAD's ability to process DNS requests, apply DNS firewalling and maintain DNS logs by obscuring your DNS activity. You may disable these features in your browser:
- FireFox: Go to Settings, then Privacy & Security. Scroll down to HTTPS-Only Mode and disable it.
- Chrome: Type "Chrome://flags" in the URL bar and search for DNS. Find "Async DNS resolve" and disable it, and "Secure DNS Lookups" and disable it.
- Edge: Type "Edge://settings" in the URL bar or click on "Settings" in the dropdown menu and select "Privacy, search and services." Under "Security" find "Use secure DNS to specify how to lookup the address for websites" and disable it.
Having these settings enabled thwarts your attempts to control your Internet traffic by domain name by hiding your domain name requests (which are sent out everytime you go to a website) by using HTTPS to send the requests, which is not the same as HTTP and uses SSL to encrypt the request, essentially making it impossible to tell what domain information your computer is requesting from the DNS registries. These so-called "secure DNS" features also direct your DNS requests to a DNS resolver of the browser maker's choice, rather than getting the information directly from the authoritative DNS registries (which is what LAD does). The interesting thing about their "secure DNS" is that in some situations they may deliver different results from each other and from the official DNS registries.
Additionally, by using their "secure DNS" you allow them to track your device, your browser, where you go, tag your browser and build a profile of your Internet use, since your requests are processed through their DNS resolver servers, rather than the official DNS registries. In normal DNS processing through the official registries, no one keeps tabs on your DNS requests. Typically it is also more difficult for the authoritative DNS registries to be tampered with.
For information on how a device's domain name settings interact with DNS firewalling and White and Blacklisting, please see Access Controls / Parental Controls.
<< Configuring a Wireless Network | Groups >>
