LateralAccessDevice
takes you back to before the Internet
How It Works | Download LAD | Support | LAD Security | Features & Uses | Resources | Members | User Guide
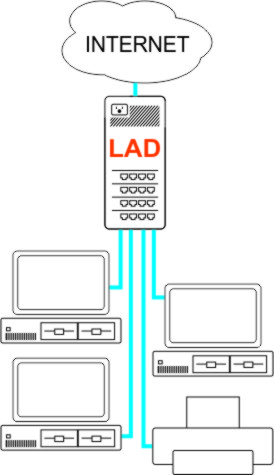
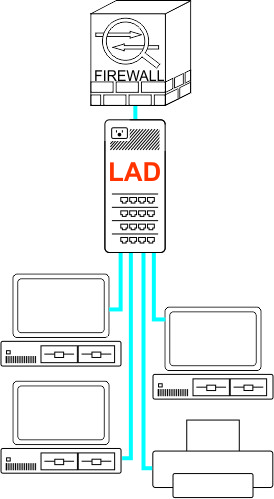
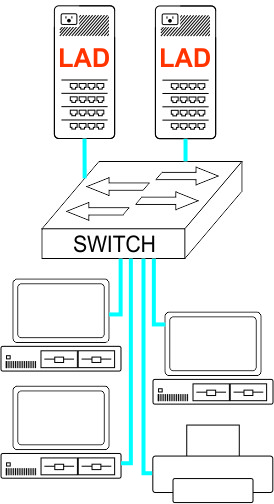
LAD for NetworkingLateralAccessDevice is commercial-grade software designed to be used by anyone, from someone with little or no experience setting up networks to software developers and professionals who need robust solutions to help them in their daily professional life. LAD is a purpose-built, multi-dimensional tool for network management and control (among other available functions, including SIP server and VoIP PBX and DNS). It combines the features and functions of a firewall, switch, router, packet capture appliance and DNS server with network monitoring and visualization and incorporates Lateral Firewall, LateralDNS and LateralTime technologies, with an emphasis on providing visibility and controlling access. In simpler terms, it is an all-in-one networking system that you run on your own hardware. InstallationLAD runs on a separate computer, your own hardware, in fact, so that it runs externally from all the computers and other networked devices that it manages and monitors. To install LAD on your designated computer, which may be any compatible computer, whether new, a decommissioned desktop or a minicomputer with multiple ports, simply create a bootable USB stick and boot up the computer from that USB stick. The software initializes the hardware and installs itself automatically. All you have to do is sit back and wait a few minutes. DeploymentYou may use LAD as a drop-in replacement for or in addition to a router, wireless router for 2.4Ghz, 5G and 6G, firewall and other networking equipment. In some cases, for example, where you have specifically configured networking equipment that you do not wish to change out, LAD operates seamlessly and transparently right along side it. In other circumstances, it could replace the old router or firewall entirely. Since you run it on your own hardware, you have control over how many ports you have for connecting equipment to it, as well as how much storage it has. LAD may be placed anywhere on the network where you want more monitoring and control over your computers' communications, whether it be over their conversations with Internet or with each other.
OperationOnce you have LAD up and running, log in to see all the active devices and computers, automated reports on Internet and network activity and the websites, URLs and IP addresses your computers and other assets on the network have accessed, then take control. LAD's controls are intuitive and easy-to-use, with no need to learn any special programming language to tell it what you want it to do. For some tips, see Getting Started with LAD. |